Secured Communication Solutions in Defense: In the digital age, security is now a must. Given the volume of data being transmitted online, every step must be taken to avoid security breaches.
Underlying technologies like real-time communications, routing, and security must be dependable and real-time in the first place to have a dependable system and good real-time performance. In that instance, a crucial component of wireless networks that offer mobile customers quality of service (QoS) is secure communication.
Secure communication refers to the techniques and tools used to guarantee that data transferred between parties is shielded from unwanted access, interception, or manipulation.
The defense industry depends on safe, interoperable technologies for everything from satellite communications to encrypted radio transmissions to safeguard sensitive information and preserve tactical advantages.
According to verified market reports, The size of the secure communication market was estimated at USD 98.9 billion in 2023 and is expected to increase at a compound annual growth rate (CAGR) of 9% from 2024 to 2030, reaching USD 149.8 billion.
A variety of services and technologies aimed at safeguarding data availability, confidentiality, and integrity in digital communications are included in the secure communication market.
The need for secure communication solutions has increased as the globe grows more linked. This is due to the necessity for enterprises to protect sensitive data, the growing frequency of cyber threats, and regulatory compliance requirements.
The significance of secure communication, its development, essential components, and the most recent developments that improve the security of military communication systems are all covered in this blog.
Evolution of Secured Communication in Defense
A radio-controlled boat that enabled safe communication between transmitter and receiver was demonstrated by Nikola Tesla in Madison Square Garden in 1898.

In Africa, America, and some areas of Asia, rudimentary techniques like smoke signals and drums were employed thousands of years ago to begin the history of communications.
In Europe, the first fixed semaphore systems appeared by the 1790s. Even though semaphore systems were a major advancement, ensuring that signals were not intercepted remained difficult.
The field of defensive communication saw a radical change in the late 1800s. This change was marked by the introduction of electrical telecommunications technologies and contact center certification procedures.
Systems for electrical telephony began to appear in the late 1830s. By 1876, communication had advanced significantly when Thomas A. Watson and Alexander Graham Bell demonstrated the electric telephone in Boston.
Although the electric telephone changed the game, the defense communication industry was about to enter another revolutionary age as the 20th century drew near. The development of radio communication characterized this era.
The widespread use of radios on the battlefield during World War I changed coordination and communication tactics.
Reliable communication between ground forces, artillery units, aircraft, and headquarters was made possible by portable radios.
Radio communication was essential to air and naval operations during World War II, maintaining this strategic edge.
However, there were difficulties in the early days of radio communication. The technology’s shortcomings included frequency jamming, short communication ranges, and a lack of encryption.
Notwithstanding the difficulties, defense communication entered the era of wireless telecommunication thanks to the early introduction of radios.
Space Age and Satellites for Defense
Defense communication capabilities were significantly improved with the development of satellite-based communication in the 1950s, coinciding with the space age.
Instantaneous global information transport is made possible by communication satellites in geosynchronous orbit. This significantly improved the ability to share intelligence and transmit data in real time.
Communication satellites improved monitoring and reconnaissance during the Cold War.
The strategic importance of satellites was demonstrated by the US’s Corona spy satellite program, which transmitted photos from space and provided important photographic intelligence.
Satellites have been used more and more throughout the years to help military operations by improving communication, weather monitoring, and navigation.
Even though satellite communication was revolutionary, defense communication saw a further transformation at the close of the 20th century as a result of the development of digital technologies and the internet.
Internet and Digital Communication Platforms
Digital communication advanced quickly in the late 20th century. The GSM mobile communication standard was up and running by 1991.
The introduction of the Mosaic graphical web browser in 1993 opened the door for platforms for online conversation.
Defense communication started incorporating increasingly advanced technologies and using new communication techniques as the internet became more widely available and technology advanced.
Key Technologies in Secure Communications
A variety of technologies are used by contemporary secure communications systems to safeguard data transfer across several platforms.
These technologies guarantee that communications are protected from interruption or unwanted access, encrypted, and authenticated.
Among the most important technologies enabling secure communications in military operations are the following:
End-to-End Encryption: Data is encrypted at the source and stays safe until it gets to the intended recipient thanks to end-to-end encryption.
To protect sensitive data, encryption techniques like RSA and AES-256 are frequently utilized. Even if opponents manage to access the communication channels, this stops them from intercepting and decrypting military messages.
Quantum Cryptography: A new technology called quantum cryptography has the potential to completely transform secure communications.
Quantum cryptography offers an encryption technique that is theoretically infallible by utilizing the concepts of quantum mechanics.
Two parties can safely share encryption keys thanks to quantum key distribution (QKD), which makes sure that any effort to intercept the key is quickly discovered.
Secure Satellite Communications (SATCOM): In military communications, SATCOM is essential, particularly in remote or combat zones.
Encrypted data transmission is used by secure SATCOM systems to guard against adversary interception.
Commanders can coordinate operations around the world thanks to advanced SATCOM technology, which offers real-time communication capabilities over large distances.
Software-Defined Radio (SDR): Military radios can instantly adjust to new frequencies and encryption standards thanks to SDR technology.
Even if enemies try to jam or intercept signals, this adaptability guarantees that communication networks stay safe.
Under challenging circumstances, SDR systems can change encryption algorithms, switch frequencies, and continue to communicate without interruption.
Zero Trust Architecture: Military communication systems are progressively implementing zero trust security concepts.
Even inside the network perimeter, no user or device is intrinsically trusted in this method. The risk of illegal access or data breaches is decreased by authenticating and encrypting each communication request.
Public Key Infrastructure (PKI): PKI uses cryptographic keys and digital certificates to enable safe connections.
PKI is used by military organizations to authenticate people and devices, guaranteeing that only individuals with the proper authorization can access sensitive data or communication channels.
PKI also protects data integrity by guarding against message forgery and manipulation.
Secure Messaging Platforms: The usage of secure messaging technologies to facilitate encrypted, real-time communication between military personnel is growing.
These technologies, which offer secure audio, video, and message communication and are constructed with military-grade encryption, guarantee that no private information is compromised while operations are underway.
Frequency Hopping Spread Spectrum (FHSS): FHSS technology quickly switches between various frequency channels to prevent jamming or interception of military radio communications.
Even in the face of threats from electronic warfare, military radios can retain safe communication channels by switching between several frequencies.
Types of Communication Systems in Defense
Defense communication systems are varied and designed to satisfy intricate air, sea, and land operational requirements. Below is a summary of the primary kinds:
Radio Communication Systems: These systems, which support several frequencies for voice, data, and secure transmission, serve as the foundation of field communication. They consist of high-frequency radios for long-distance communication, satellite communication, and handheld radios.
Satellite Communication (SATCOM): Units in remote areas can stay connected because of SATCOM’s worldwide reach. Coordination between air, land, and naval forces, as well as real-time data sharing and navigation, depend on it.
Software-Defined Radios (SDR): To guarantee interoperability across several military branches, these radios have the capacity to dynamically switch frequencies. Because of its adaptability to different communication protocols, SDRs improve coordination in activities involving multiple branches.
Tactical Communication Networks: Tactical networks provide real-time situational awareness and data transfer between troops, vehicles, and command centers. The U.S. Army’s WIN-T (Warfighter Information Network-Tactical) is one example.
Secure Communication Systems: Encrypted channels are necessary for military communication in order to defend against interception and guarantee data confidentiality. Access control and sophisticated cryptography are used by modern military systems to protect communications.
Cryptographic solutions for Secure communication
The method of safeguarding communications and information by using codes that only the intended recipients can decipher and process is known as cryptography.
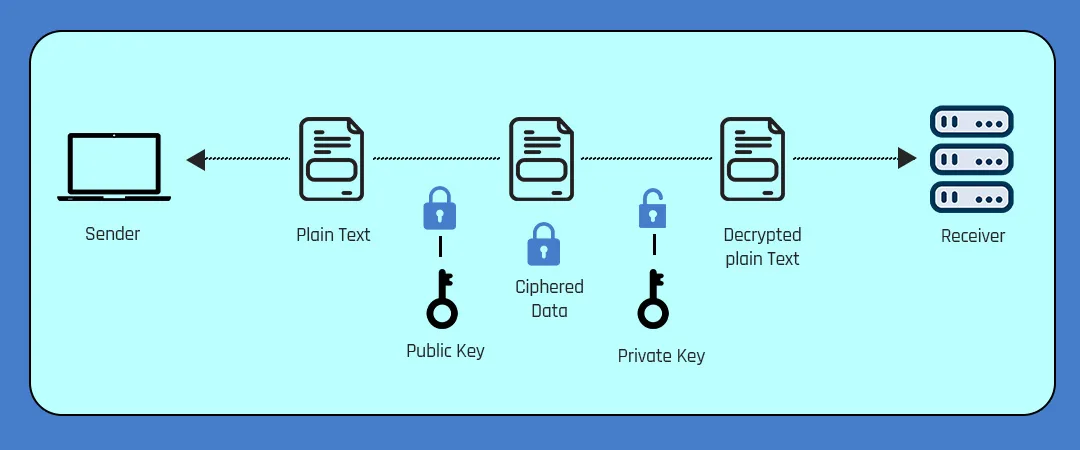
Symmetric vs. asymmetric encryption in defense
Symmetric encryption offers a fast technique perfect for managing massive data volumes in real-time since it only requires one key to encrypt and decrypt data.
Symmetric encryption is effective and uses algorithms like AES resistant to brute-force attacks, so defense systems frequently use it for data at rest. Distributing the key securely is a major challenge, too, because if it is not sufficiently safeguarded, interception might jeopardize the system.

Asymmetric encryption, on the other hand, improves security, particularly for data in transit, by using a pair of keys: a public key for encryption and a private key for decryption.
By eliminating the requirement for direct key exchange, this method lowers the risks involved in key distribution and adds additional stages of authentication and verification for digital signatures.
It is frequently used to provide secure channels and for applications where security is more important than speed, including command and control communications in defense networks, even though it is slower than symmetric encryption.
Role of Artificial Intelligence in Secured Communication
Customer identification

When a consumer calls a business, the person in charge of his/her case or who can respond to his/her question is not necessarily the first person to answer.
However, this means that any employee who speaks to them must ask the same questions to confirm their identity and guarantee secure contact.
Customers may become frantic as a result of having to repeatedly repeat their information, which could ruin their experience.
AI speeds up and improves the accuracy of this procedure in this way.
A virtual agent, also known as a callbot or chatbot, will greet users, ask the right questions to ascertain the accuracy of the information, and learn the purpose of their inquiry before forwarding the interaction to the agent most suited to handle it.
However, artificial intelligence goes one step further and verifies the identity of the customer during calls using speech biometrics technology. This stops fraud and unauthorized individuals from accessing the data.
Data is not stored

Security is not always guaranteed when some procedures are carried out by hand. Employee processing of data makes it possible for the data to be stored, making it vulnerable to third-party interception.
While it is true that these solutions promote safe communication when delivering sensitive information like credit card numbers, this does not imply that risks are eliminated or that employee intervention is no longer necessary.
For instance, a lot of businesses have chosen to charge credit cards while on the phone.
Businesses can benefit greatly from this feature since, on the one hand, it makes things simple for customers and enables them to close deals quickly.
However, it also enables them to do things like charge customers in advance for the use of a service or schedule automated billing calls to collect overdue debts from clients and immediately erase the obligation.
Conversational AI systems provide an extra degree of protection in this procedure.
The customer’s call will be routed by the agent to an intelligent system, which will ask for his payment information and process it with the bank immediately without keeping a record of it.
Furthermore, staff members will always be able to observe where the user is in the process and verify that the transaction is being completed correctly.
Security standards

In connection with the previously stated, an AI solution needs to meet minimal security requirements in order to be able to carry out tasks like accepting card payments over the phone.
Among these is the PCI-DSS standard, which permits the creation of a secure environment throughout the transaction and is required for all businesses that accept credit card payments in any way.
Furthermore, we discovered that these technologies continuously analyze data in real time as an extra measure to guarantee a secure connection.
While it is desirable to use every resource to stop data leaks, this isn’t always the case. Therefore, putting in place the tools to identify harmful behavior early on is just as beneficial as prevention.
AI can identify any questionable activity in this situation and notify staff members right away, allowing them to investigate and take action before the issue worsens.
Reduction of errors

The ability of bots to learn from every encounter and, consequently, reduce errors is the final crucial aspect of the relationship between artificial intelligence and security.
By using concepts like Machine Learning (Continuous Learning), virtual agents can get better with each interaction, evaluating and understanding data and creating patterns to prevent future errors.
Use of Blockchain Technology in Defense Communication

Blockchain is becoming a game-changer in a time when secure communication is crucial.
Adopting systems that can handle the increasing complexity of contemporary threats is essential to the future of military communication.
Blockchain is well-known for its involvement in Bitcoin, but it has also become a vital defense mechanism for guaranteeing safe, robust communication networks.
However, in what specific ways may blockchain transform military communications?
Decentralization – Eliminating Single Points of Failure
Blockchain functions on a decentralized network, as opposed to centralized systems, in which data is dispersed across several nodes rather than kept in one place.
This implies that the integrity of the entire system is unaffected even if one node is altered or compromised.
This decentralized architecture greatly lowers the possibility of cyberattacks bringing down whole communication networks for the defense industry.
Immutability – Ensuring Tamper-Proof Communication
Every message received through military channels is guaranteed to remain unaltered by blockchain’s intrinsic immutability, which states that once data is recorded, it cannot be changed.
In high-stakes defensive situations where communication integrity could mean the difference between life and death, this characteristic is essential.
Transparency and validity may be guaranteed at every stage by tracking and verifying messages during transmission.
Real-Time Transparency- Building Trust in Critical Operations
Blockchain technology offers real-time insight into the communication process, which is crucial for military operations that demand exact coordination.
Defense forces can keep an eye on every step of communication transmission to make sure it hasn’t been intercepted or changed by incorporating blockchain.
During crucial missions, this openness fosters confidence in the communication system and enables quicker and more assured decision-making.
Advanced Encryption – Fortifying Against Cyber Threats
Blockchain technology secures data using cutting-edge cryptographic algorithms, virtually eliminating illegal access.
Blockchain’s encryption provides an unparalleled level of security for military communications, as nation-state actors or rogue entities are always looking to exploit vulnerabilities.
Through its distributed ledger, blockchain continuously strengthens security, protecting important military data in contrast to conventional encryption techniques that can be cracked over time.
In defense, blockchain is more than a trend; it’s a need. Defense forces throughout the world may defend themselves against increasing cyber threats by incorporating blockchain technology into their military communication systems, guaranteeing that their communications will always be safe, open, and impenetrable.
Cybersecurity Measures in Defense Communication

Here’s an overview of the critical role cybersecurity plays in defense,
Protection of Sensitive Data: Protecting sensitive, mission-critical, and classified data requires cybersecurity. These consist of intelligence reports, communications, military plans, and personally identifiable information (PII). Data breaches or unauthorized access can have serious consequences.
National Security: Cybersecurity is crucial for protecting a country’s security interests and sovereignty in the context of national defense. Cyberattacks against government organizations, military installations, or vital infrastructure can cause operational disruptions and present serious risks to national security.
Defense Against Cyber Warfare: To protect against state-sponsored cyberattacks, countries need to invest in strong cybersecurity measures in light of the advent of cyber warfare. To identify, lessen, and address such dangers, cybersecurity is essential.
Protection of Critical Infrastructure: Protecting key infrastructure sectors like energy, transportation, healthcare, and financial services requires cybersecurity. Attacks on these industries may have serious repercussions, such as upsetting the country.
Counterintelligence: Cybersecurity aids in detecting and stopping foreign actors’ espionage attempts to steal defense information. Insider risks that could jeopardize national security are identified and eliminated with its help.
Securing Communications: To coordinate operations and exchange sensitive data, military and defense organizations depend on safe, encrypted communication networks. The availability, confidentiality, and integrity of these communications are guaranteed by cybersecurity.
Advanced Threat Detection: Advanced threat detection capabilities offered by cybersecurity tools and technology help defense organizations recognize and quickly address malware, cyber threats, and cyberattacks.
Resilience and Continuity: Planning for cyber resilience guarantees that defense organizations can carry out their missions even in the event of system failures or cyberattacks. Strong backup and recovery protocols are required for this.
Military Cyber Units: For both offensive and defensive cyber operations, numerous defense organizations set up specialized cyber units. These units safeguard vital defense assets, build cyber capabilities, and carry out cyber investigations.
Cybersecurity is essential to the defense industry’s capacity to safeguard sensitive data, vital infrastructure, and national security interests.
It makes it possible for the military to function safely, efficiently counteract cyber threats, and stay prepared in a world that is becoming more digitally connected.
Secure Satellite Communication in Defense

The importance of secure satellite communications (SATCOM) has grown in the linked world of today.
Data transmission via satellite networks is essential for business continuity, disaster relief, and military activities.
To meet the demands of commercial, military, and governmental users, Secure SATCOM offers dependable, secure, and real-time communications.
End-to-end SATCOM communications are safeguarded and observed in accordance with the strictest resilience, integrity, availability, and reliability criteria thanks to Secure Satellite Communications (SATCOM).
Through initiatives like the Enhanced Mobile Satellite Services (EMSS) and Protected Tactical Enterprise Service (PTES), the U.S. Department of Defense is also updating its SATCOM architecture.
The goal of these initiatives is to provide warfighters worldwide with sophisticated, jam-resistant communications.
In government communications pertaining to security and the military, satellite communications are essential.
When alternative ground-based communication methods are unavailable, unreliable, or impractical, they are employed.
The ability of states to react independently and promptly to international defense, security, humanitarian, and emergency crises depends heavily on satellite communications.
Role of 5G in Defense Communication

The necessity for fast, dependable networks like 5G to link defense operations’ robots, sensors, drones, and autonomous vehicles has increased due to the global expansion in modern technology.
5G’s fast speed, machine-to-machine communication, and real-time connectivity are essential for security services’ intelligence and surveillance operations.
For military and government applications, it allows frequency hopping in tactical radios by utilizing the ultra-high frequency (UHF) spectrum, which spans from 300 MHz to 3 GHz.
For instance, 5G’s modulation capabilities are essential for smart bases (which require low power and long range) and border surveillance (which requires high power and low latency).
Network capacity is also increased by the introduction of tiny cell stations. Network design, coverage, communication, and throughput are all improved by 5G’s cutting-edge features, which include beam-forming antennas, 5G New Radio (NR), Cellular Vehicle-To-Everything (C-V2X) technology, Network Functions Virtualization (NFV), and MIMO antennas.
These technologies increase the productivity of defense mechanisms by enabling immersive services like mobile cloud and ultra-high resolution 3D video.
Thus, the technological advancement of 5G offers substantial prospects for market expansion in the defense industry.
Applications of 5G in Defence
The battlefield is expected to undergo a digital revolution thanks to 5G. The availability of extremely high data rates and nearly instantaneous transfers allows for this competitive advantage.
Let’s examine a few ways that 5G networks are being used in defense:
Massive Improvement in Tactical Communications
5G is intended to give military personnel in the field smooth and safe communication links. It promises extremely dependable connectivity, enhancing situational awareness and operational efficiency for everything from real-time battlefield cooperation to ad hoc networks in an emergency.
Network Slicing – Segmentation and Prioritization
To guarantee that vital processes receive the best possible network resources, defense networks typically need to be segmented and prioritized quite strictly.
Because 5G networks may be divided into multiple layers, distinct user groups and apps can function independently while yet ensuring security and quality of service.
Autonomous Vehicles & Drones
The connectivity and data transfer needs of drones and driverless cars can be met by 5G networks, enabling remote control and operation in combat situations and lowering the hazards to human operators.
Logic Fruit offers high-performance IPs for FlexRay, CAN, and LIN protocols with safe real-time communication required for automotive and defense applications. The IPs are optimized to deliver reliability with minimal power consumption, thereby facilitating fault-tolerant high-speed data transfer in FlexRay, low-latency, and robust communication in CAN, and low-cost data transfer in LIN-based simple systems.
5G-powered Augmented Reality for Training
Augmented Reality (AR) is one of 5G’s capabilities. By simulating different training scenarios, augmented reality technology can help military personnel in the field increase situational awareness and training efficacy.
Real-time Enemy Surveillance
Armed forces can implement surveillance systems that offer real-time intelligence on adversary movements and activities because of 5G technology’s high-speed data transmission and minimal latency. Consequently, this improves tactical decision-making and intelligence.
Intersection of NTN and 5G in defense
Satellite communication can also be made possible via 5G. It can provide vital connectivity for first responders and tactical military users, as well as expand coverage to far-flung locations. Non-terrestrial networks (NTNs) enable military operations in previously unreachable areas by utilizing space-borne assets to provide ubiquitous cellular coverage.
Specific use cases of 5G in the Defence Sector
Let’s now examine particular instances where different military forces around the globe are taking advantage of 5G’s promise to attain significantly higher levels of operational effectiveness and strategic adaptability in battle.
Indian Armed Forces
- The Indian Army is at the forefront of using 5G technology to improve communication infrastructure and operational capabilities. They are creating military-grade 5G applications in partnership with MeitY to improve intelligence collection and situational awareness.
- The Army intends to roll out 5G networks in border regions through projects like establishing a 5G lab at MCTE and collaborations with organizations like IIT Madras, reiterating its dedication to updating military plans and safeguarding national boundaries.
USA Department of Defense
- AR and VR applications for improved training and situational simulations are among the many use cases for 5G networks that the US DoD has identified.
- 5G networks are also used by businesses to link and control IoT sensors and devices, enhancing situational awareness and decision-making.
- Additionally, these networks facilitate communication among unmanned systems, drones, and driverless cars, improving military operations’ coordination and control.
Tactical Data Links (TDLs) and Secure Networks
One important real-time military communication service is Tactical Data Links (TDL), sometimes known as Tactical Digital Information Links (TADIL).
One of the numerous standards that are used to offer TDL, such as Link 11, Link 16, Link 22, and J-Message, frequently refers to TDL. A very quick introduction to TDLs is given at the beginning of this publication.
The fundamental idea behind TDL is the sharing of short, standardized messages via a common communications channel, specifically HF radio and UHF.
Sharing the position of hostile and friendly mobile units using data from radar and other sources is a fundamental function. Since this tracking feature is essential to TDL, the service is frequently referred to as “tracks.”
TDL Standards and Names Used
This section provides a quick overview of TDL, which is frequently cited by the standards in use.
There is enough unclassified information to provide a comprehensive knowledge of TDLs, but many of the essential TDL requirements are unavoidably secret.
Link 11 – The original TDL, which is still in use, is Link 11. Ralph Benjamin created TDL at the Admiralty Surface Weapons Establishment (ASWE) in the United Kingdom in the 1950s and 1960s. Later on, NATO adopted and standardized it.
It operates at a fixed speed over HF and UHF, sending 24-bit messages in a 30-bit payload. It can operate in broadcast mode or half duplex transmission between two nodes.
In a half-duplex, network members can transmit one after the other thanks to a controlling node’s “roll call” mechanism.
Link 16 – A more advanced and contemporary TDL, Link 16 is mostly utilized for aviation communication.
It uses TDMA to share a single fixed frequency channel and functions in a particular UHF sector. Link 16 offers audio, text messaging, and picture transfer in addition to the standard TDL short-format communications.
J Message – One often used library of TDL messages is J Message or J Series Messages. TADIL-J, a variant of Link 16, is where the “J” originates.
Other versions, like M Message, are occasionally cited in a similar way. A clear method for referencing TDL messages is provided by J Message.
SIMPLE – STANAG 5062 specifies SIMPLE (Standard Interface for Multiple Platform Link Evaluation). TDL message transmission over IP is made possible via SIMPLE.
In practice, JREAP C is preferable, although SIMPLE and the framework it is based on seem to be outdated.
JREAP – TDL messages can be sent across long-distance networks via the Joint Range Extension Applications Protocol (JREAP).
JREAP makes it possible to integrate with strategic networks, whereas the fundamental TDL protocols are made for tactical networks.
Three variations of JREAP exist. Constrained links are supported by JREAP A (half duplex) and JREAP B (duplex). To function across IP networks, JREAP C offers TCP and UDP protocols.
Link 22 – Link 22 is a contemporary, naval-focused substitute for Link 11. It can also be an upgrade path for Link 16 systems because it utilizes Link 16 features. The NATO Improvements to Link 11 (NILE) program created Link 22, which is also known as NILE.
Key features of Link 22:
- Supports J Messages – compatible with Link 16
- Operates over HF and UHF, fixed speed, and fixed frequency.
- Used a Dynamic TDMA (DTMA) approach for members of a network.
- Allows nodes to join a network (late network entry).
- Supports multiple interconnected networks (a Super Network) and relay between networks.
- Messages can be directed to a list of nodes, all nodes on the network, or all nodes on the Super Network
- Error correction
- Resilient to node loss
- Messages have priority.
- Congestion management, giving preference to higher priority messages.
- Message creation time and perishability (when a message is no longer valid).
Secured Mobile Communication in Defense

In the field of military cryptography, secure mobile communication devices are a significant breakthrough.
By enabling encrypted communication streams via mobile devices, these technologies guarantee the confidentiality of sensitive data while processes are underway.
They build a digital stronghold against illegal access and interception by using cutting-edge encryption techniques.
Secure communication devices encrypted mobile networks, and Mission Critical Services (MCS) based on 4G and 5G networks are examples of key technologies.
Encryption, which includes protocols like Elliptic Curve Cryptography (ECC) and Advanced Encryption Standard (AES), is a key component of secure military communication.
By securing data sent over communication channels like satellites and private mobile networks, these protocols make it more difficult for unwanted parties to access or alter data.
Multi-frequency and anti-jamming technologies are also included to guarantee continuous contact in unfriendly settings.
Logic Fruit’s AES-256 IP Core provides high-security data encryption, transforming plaintext into ciphertext using multiple transformation rounds and a 32-byte round key.
Compliant with NIST, this IP core applies Rijndael encoding with a 256-bit block and key size, making it ideal for applications demanding strong data protection.
The Joint Tactical Radio System (JTRS) and Secure Terminal Equipment (STE) are two examples of the modern era.
While JTRS improves interoperability with strong encryption capabilities, which are essential for joint missions across many branches, the STE allows secure voice and data transfer across multiple military networks.
Securing Communication During Joint Military Operations

In order to accomplish a shared goal, several branches of the armed services coordinate their efforts in joint military operations.
Interoperability, or the capacity of various military units to collaborate effectively, is one of the crucial factors that determines the success of such operations.
Since cooperation and communication are essential to the success of any combined military operation, this is directly related to efficient information exchange.
For collaborative military operations to be successful, information exchange is essential. Making informed judgments in dynamic operational contexts requires accurate and fast information sharing.
A comprehensive understanding of the whole situation is made possible by good information sharing, which enables various military units to coordinate operations and effectively react to changing conditions.
Information exchange transcends the conventional divisions of individual branches in the setting of combined military operations.
The several units engaged share real-time updates, logistics information, and intelligence.
This cooperative strategy guarantees that every member of the joint force is knowledgeable and capable of making a valuable contribution to the mission as a whole.
Role of Cloud technologies in defense Communication

Modern warfare relies heavily on information dominance, and in an ever-evolving digital environment, cloud technology investment is essential to preserving these defense capabilities.
To keep ahead of their enemies during combat, armed forces need to collect and analyze vast amounts of data.
However, the concept of warfare has expanded beyond conventional land, sea, and air confrontations to include several interconnected forms of conflict, such as cyberwarfare, information warfare, and space warfare.
The influences of technology, which speed up the waging and management of conflict, further complicate the evolution of warfare.
However, information technology systems must be able to handle vast amounts of data quickly to make the kind of decisions that modern combat demands (Defence One, n.d.).
To maintain the information advantage that is the foundation of successful combat, European forces must embrace new technology, particularly cloud computing, as it is surpassing these outdated IT systems.
Investing in cloud computing is essential to preserving information superiority since it is anticipated to be the foundation of all future digital defense capabilities.
Because it may house a variety of computing tools that support information superiority through situational awareness and aid in effective decision-making during combat, the cloud is more than just a platform for storage.
Conclusion
Secured communication solutions have become critical in recent defense operations to promote confidentiality, integrity, and availability across the various channels of military communication.
Defense technology involving encryption, AI-based threat detection, blockchain, and 5G is continually enhancing the dependability and resilience of systems.
Defense forces invest in advanced cryptographic methods, robust cybersecurity measures, and the innovation of secure satellite and tactical data links to ensure communications are uncompromised and adapting to emerging threats.
When defense operations are placed within increasing security demands, such solutions are able to further protect information and keep response times to a minimum, with minimal disruption within complex coordination mechanisms.
Frequently Asked Questions
How do you ensure secure communication?
Use SSL/TLS certificates, VPNs, and encryption (AES) to provide private and secure communication between computers.
Put access restriction and robust authentication (such as multi-factor authentication) into practice. Use secure protocols (e.g., HTTPS, SFTP) and firewalls to monitor and manage traffic.
What is the Defence communications strategy?
Expanding and improving the Australian Defence Force and Australian Public Service to become a best-in-class workforce and lowering dependency on contractors are the three main themes that the Strategy employs to drive Defence’s digital agenda. Utilizing the strength of well-known international platforms.
What is Defence communication?
The Defence Communication Network is a strategic, highly secure, and scalable system that spans the entire country of India and allows the Army, Air Force, navy, and Special Forces Command to share situational knowledge for quicker decision-making.
What is the principle of communication for Defence?
COMMUNICATION FOR DEFENCE
This is where a combination of capability and process is required to ensure that messages are coherent and co) coordinated. Messages also need to be tailored in the way most appropriate to their audience to have influence.
Which method is used in military communication?
Military communication usually consists of radio, telephone, and digital communications.










